The Potential Economic Crisis:Internet security is terrible today and yet somehow still getting worse every day, despite perpetual patching on a piecemeal basis. The potential for a major cybersecurity-induced economic catastrophe is already quite real and growing inexorably, while all efforts at prevention in the past decade have failed. This dire situation is starkly summarized in “Tinker, Tailor, Soldier, Hacker” in THE WALL STREET JOURNAL of April 21, 2010.
President Obama declared in early 2009 that the “cyber threat is one of the most serious economic and national security challenges we face as a nation” and that “America’s economic prosperity in the 21st century will depend on cybersecurity.” Nevertheless, the comprehensive White House CYBERSPACE POLICY REVIEW released in April, 2009, has no clearly defined, comprehensive solution, just much more patchwork in reaction to specific attack outbreaks as they occur; see also Securing Our Digital Future. One year later, today, we still cannot protect ourselves, as noted in the 2010 Annual Intelligence Threat Assessment.
The lack of progress despite expenditures in the billions and a decade of extreme effort strongly suggests that some basic problem so simple it has been overlooked. It turns out the basic problem is really not the Internet itself. The Internet is, after all, just a relatively dumb network, with almost all the intelligence located at its edge in the hundreds of millions of computers connected to it. The real problem lies in all those computers themselves. Simply put, they were not originally designed to be networked. As a result, that design has an unforeseen, but fatal flaw that has remained unnoticed for decades.
The Underlying Architectural Problem:
The fundamental problem is the archaic underlying architecture of all those computers. First designed by John von Neumann and others in 1945, the basic architecture of computers has since remained essentially unchanged at the most fundamental level. As decades passed and computer networks started to evolve in the mid 1960’s, the simple basic computer design was never reconsidered. Now, however, it has been made completely obsolete by the Internet.
Von Neumann’s now relatively ancient architecture was designed for what was essentially a gigantic programmable calculator that filled an entire large room. The design predates even the most primitive of local networks, since there were no other computers in existence in 1945 with which to connect. The exposure today of every Internet computer to the worst of millions of malicious hackers is an all too real nightmare now, but not even a daydream in 1945.
The fatal weakness of the Von Neumann architecture could not be more elemental: the computer’s basic structure as a single unit. It follows directly from that archaic unitary structure that any malware, even a lone virus, having gained entry from the anywhere in the vast Internet into any part of the computer, can potentially infect and destroy that part, or any other part, or even seize control of the entire computer.
Using the host computer’s central controller (typically integrated into a microprocessor for the past several decades), the malware can potentially erase or alter or copy any or all data files, operating code, or both, or secretly join a rogue “botnet” to use the host computer to attack other computers. (See Figure 1 again and note that all figures are schematic)
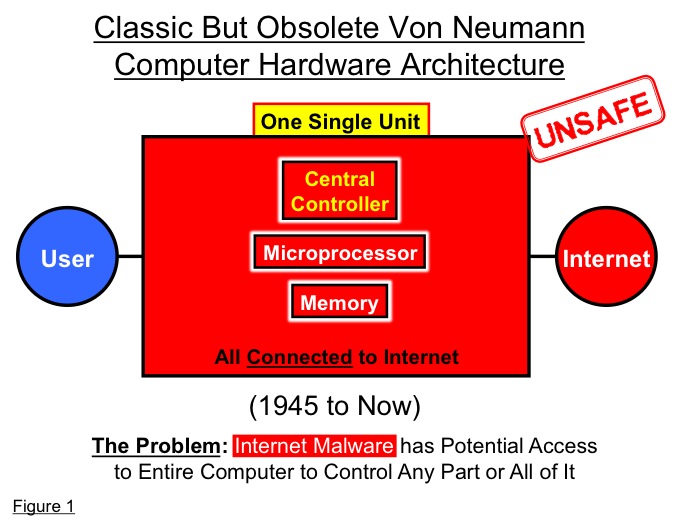
The only internal computer defense today is built out of software, but unfortunately because of software’s very impermanent nature, any defensive software is itself inherently highly vulnerable to successful attack by Internet hackers, whose work can remain undetected. All that internal software defenses provide is the illusion of safety, just as did the watertight but topless inner compartments of the Titanic.
The situation is actually so bad that the only major alternative for the past few years to make computers or networks safe from Internet attack is to disconnect them completely from the Internet. But even that approach has failed and even at the highest level, since it still allowed an extremely serious security breach in the U.S. National Defense Command network in 2007, as reported in “Sabotaging the System” on CBS 60 Minutes on November 11, 2009.
If even the radical and drastic step of disconnecting computers from the Internet does not work, then fixing the fatal Internet security defect through any other existing technical means seems almost hopeless. But even if Internet disconnection did solve the huge current security problem, the equally huge benefit of Internet connection would be lost thereby, which makes Internet disconnection impossible as a practice measure.
To sum up, the only apparent way to make computers safe today is by disconnecting them from the Internet, but even that approach can fail; and anyway, Internet disconnection is impossible due to the total dependence of the worldwide economy on the Internet.
Paradoxically, a safe Internet computer apparently needs to be connected to the Internet and also disconnected, simultaneously, which is seemingly both an impossibility and not entirely effective anyway. It seems like the evolution of the computer and Internet has left us inexorably stranded in a technological deadend with no way out.
Surprisingly, then, there is in fact a simple and practical solution to the basic Internet-connection computer security problem. However, the solution does require a very basic change to the hardware architecture of all future computers to make them Internet safe.
The Simple Architectural Solution:
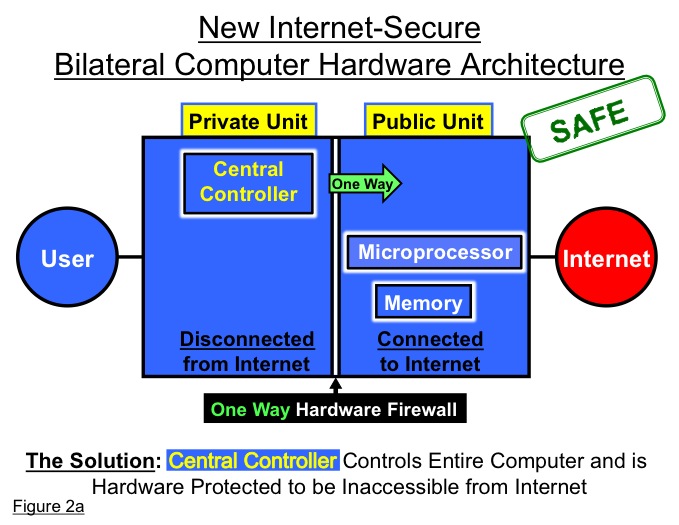
Apparently too simple to have been obvious, the radical but simple change needed in the new architecture is to make the hardware control of the computer inaccessible from the Internet or other networks. The new architecture subdivides the existing single unit computer into two separate units, roughly parallel but different. The simple new structure for computers is bilateral, like the human brain. Not essentially unitary, like the Titanic.
The two different computer hardware units are, first, a private, Internet-disconnected unit, exclusively controlled by the computer owner, and second, a public, Internet-connected unit,with a range of potential users and shared operations, but always preemptively controlled by the owner.
The central controller of the computer is positioned in the private, Internet-disconnected unit, which is made inaccessible to the Internet by a simple inner hardware firewall controlled by the central controller. The inner hardware firewall operates on the uncomplicated general rule of denying access to the private unit from the public, Internet-connected unit. (See Figure 2a)
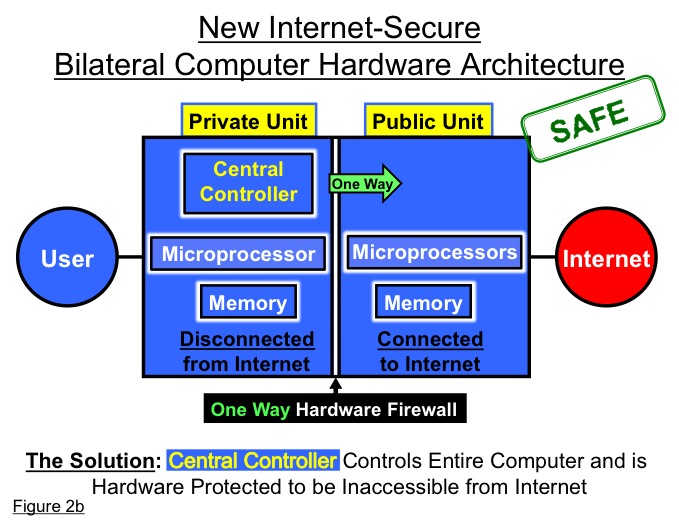
The central controller can of course be conventionally integrated a processing unit into a microprocessor and can have access to memory, particularly including non-volatile memory like Flash, also isolated on the private unit. The public unit can include one or more or even many microprocessor cores with access to memory, especially volatile memory like DRAM. A dual control hard-drive can also be used with separate hardware-controlled partitions for private and public units. (See Figure 2b)
The computer’s Internet-disconnected private unit always has preemptive control of the Internet-connected public unit. Communication between units is generally one way only, outbound from private unit to public unit. The central controller in the private unit acts sort of like a television remote controller sending control signals out to the television, but not receiving signals back (although viewing the television display).
To purge Internet malware on a routine basis, any part (or all) of the public unit DRAM that is used for any operation involving direct connection or indirect exposure to the Internet can be erased by simply interrupting power after the operation ends. This can be done by default after every Internet operation or every Web site connection, for example. (See Figure 2c)
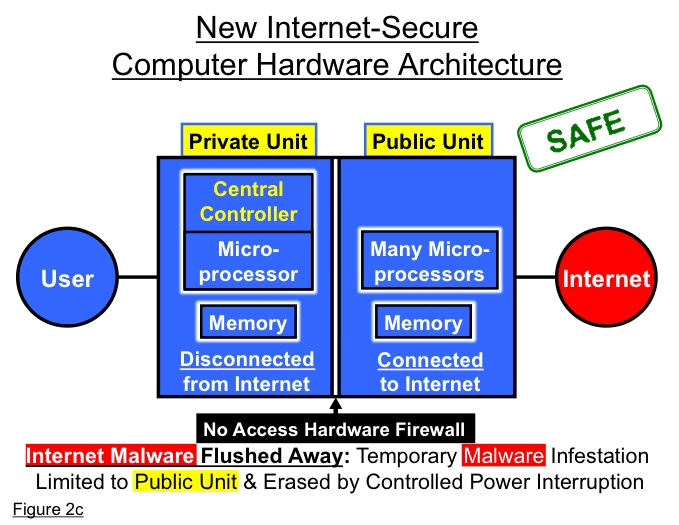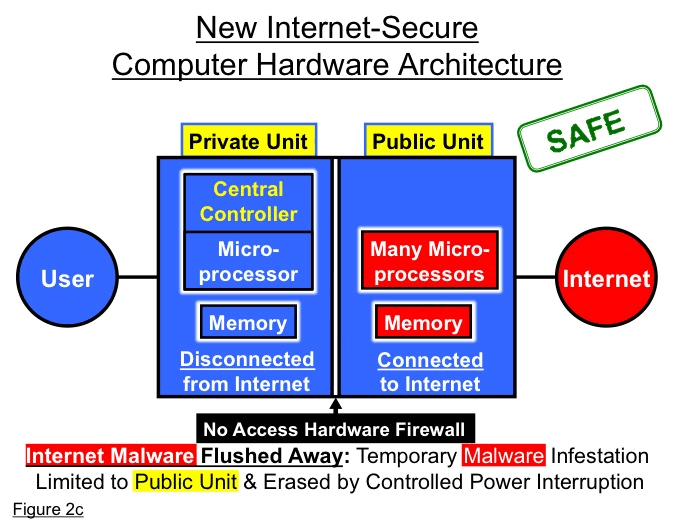
Amazingly, with this new Internet secure computer architecture, even the public, Internet-connected unit of the computer is far more secure than existing Von Neumann computers, because of both its Internet malware purging capability and its absolute protection from the Internet of the computer’s central control.
From cellphones to personal computers to Web servers and blades, the exclusive use of only new bilateral computer architecture will enable – for the first time – a truly safe level of database privacy for existing network structures and for newer “cloud” computing, allowing far better protection for sensitive medical records, financial information and email stored in the cloud, including Google’s.
It should be noted that Cloud Security Alliance’s March, 2010, report on TOP THREATS TO CLOUD COMPUTING V1.0 lists seven top threats, all of which are computer-based issues and therefore addressed by the new bilateral computer architecture.
With the new safe Internet computers, the U.S. can have a very secure, hardwired national cyberdefense with inherent natural advantages against offensive threats from the Internet. This capability is critical in maintaining peace, since the U.S. can thereby avoid the need to resort to extraordinarily risky and provocative preemptive offensive strikes against presumed enemies (in a threat environment where actual cyberattackers often cannot be identified, even for lengthy periods after their attack).
Within a few short years, with an appropriately focused but reasonable effort, it will be possible to provide a safe and stable cyberdefense both to protect the worldwide economy and to maintain peace.
ADDITIONAL COMPUTER ARCHITECTURE SECURITY ENHANCEMENTS
Multiple Inner Hardware Firewalls:
Any or all operating code, data, and hardware components can potentially be separated into as many different levels of security as potentially required by a user for additional and differentiated security. A matrix of multiple inner hardware firewalls can create many separate compartments providing different levels of security for the central controller and processing units or cores and separate parts of the operating system, application systems, and user data. (See Figure 3)
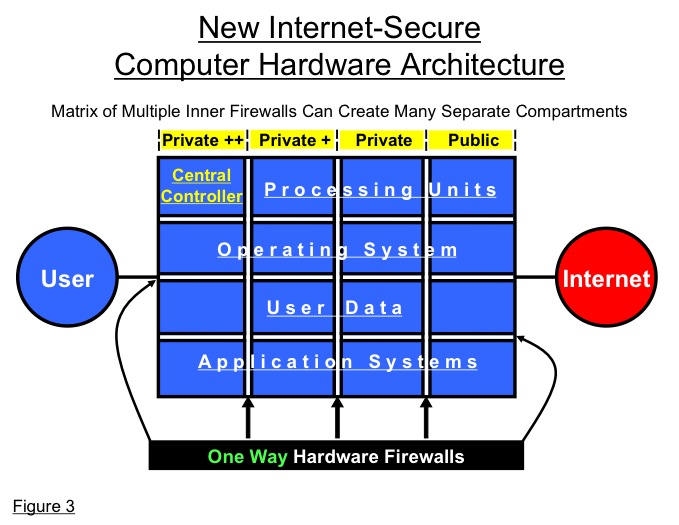
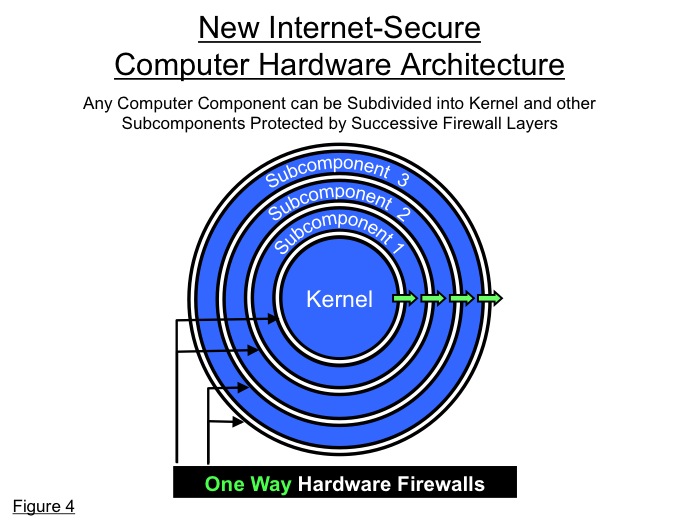
The new safe Internet computers also require an upgrade of existing software to better match the new hardware architecture, especially the multiple inner firewall design of Figure 3 above. All existing software such as operating systems, Internet browsers, and application programs must be upgraded by separating their most essential, core functions into the private, Internet-inaccessible units of the computer. The levels together form a schematic structure like that of an onion, with the smallest, simplest and most essential software kernel in the center. (See Figure 4)
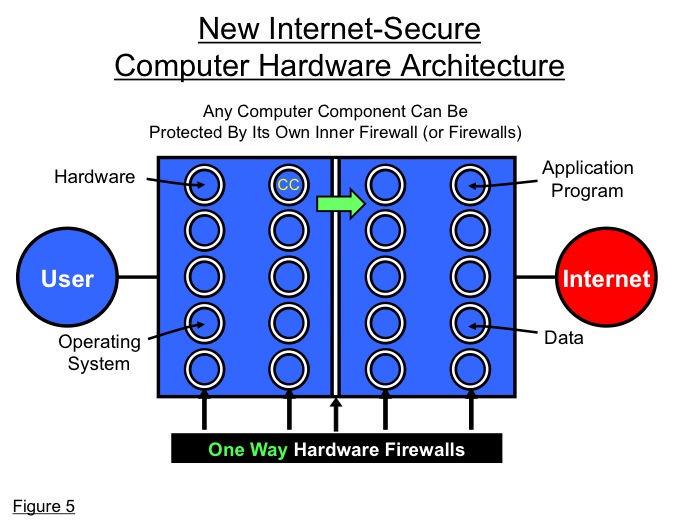
As a general rule, any hardware or software or firmware component (or group of components) of the safe Internet personal computer or smart cell phone or Web server can advantageously have its own unique hardware firewall (or firewalls). The basic multi-compartment architecture is completely flexible and scalable, and can become ever more robust as it evolves to be ever more comprehensive over time. (See Figure 5)
Faraday Cage Protection Too:
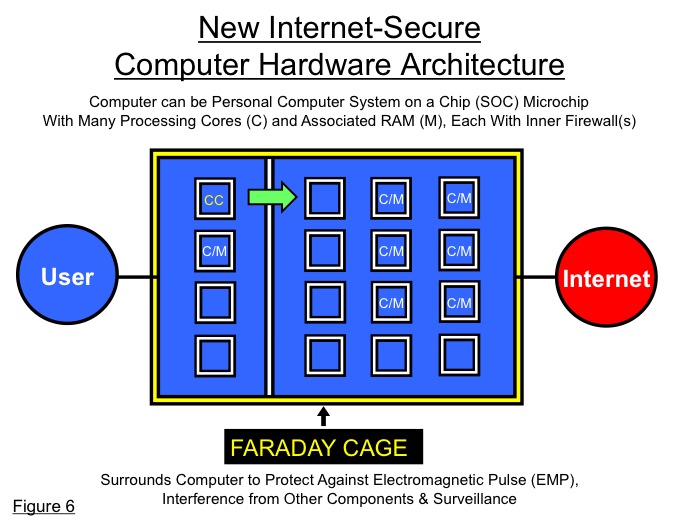
As technology evolves in the near future, many of these computer components will reside on a single microchip including the most essential components (or all components) of a personal computer on a system-on-a-chip (SOC) microchip. The SOC microchip will include many processors (cores), optimally with each having associated on-chip non-cache memory and/or shared non-cache memory.
The SOC microchip (and other microchips) should be fully surrounded by a Faraday Cage to protect it against the growing threat of electromagnetic pulse (EMP), including against entire geographic regions, and of interference from other nearby electronic components or from outside sources (perhaps like an emergency cell phone call when the car accelerator is out of control), as well as surveillance threats. (See Figure 6)
A Crash Development Program:
Because of the urgent need to counter the cyberthreat to the U.S. and throughout the world, and since there are no other viable solution options, a crash program with the highest national priority to develop the new safe Internet computer is overdue by at least a decade and should begin immediately.
But it certainly should not be anything like a Manhattan Project, which has been suggested by some authorities, since the principal program goal now – beyond truly secure national defense systems – is billions of redesigned commercial computer products, not a few atomic bombs. A crash program is clearly warranted but would be best accomplished by natural competition focused in the U.S. private sector, with initial review and leadership by DARPA, with additional support from the National Science Foundation and the Institute of Electrical and Electronics Engineers.
A successful two year safe Internet computer crash program for design and development can result in first commercial safe computers as early as in 2012.
Starting in 2012, a safe Internet computer crash program could potentially ignite a world-wide boom in demand for U.S.-made safe microchips and computers, as well as related network products. The U.S. should have an inherently vast competitive advantage in terms of trusted computer security, particularly in the U.S. design and manufacturing of safe Internet system-on-a-chip (SOC) microchips, particularly for vast and rapidly growing world-wide market for smart phones.
Cost of the New Bilateral Architecture:
On one hand the cost of developing computer and network products with the new bilateral architecture is huge, in the probable range of as much as ten billion dollars over several years. Much greater will be the cost over several years of replacing all the obsolete computers with safe Internet computers using the new bilateral architecture, since retrofitting existing computers is not feasible or cost effective.
On the other hand, the actual increased cost is probably about zero, since the cost will simply be the primary ongoing development cost of the industry for the next few years. In other words, existing development funding will be redirected to the new bilateral architecture from ongoing, lower priority development projects, such as for example developing the next 100,000 Apps for the iPhone. The unquestionable reality is that the crucial unmet need in the high tech industry world-wide today is for trustworthy security and privacy, so that is where most existing development funding should flow for at least the next several years.
To the extent that increased development funding beyond existing levels is required to accelerate the speed of transition to the new bilateral architecture, that increase should be recaptured quickly by profits from increased market share for trusted U.S. products and from the temporary increase in the size of the overall market for the several years of transition.
The U.S. high tech industry has a unique advantage over its principal competitor, China. Without regime change, which is clearly not anticipated in the foreseeable future, China cannot be a trusted microchip supplier outside of its controlled market in China.
Trusted computer security is likely to become a huge competitive advantage and therefore the one truly mandatory new feature of Internet computers as early as 2012 or 2013, since earlier Internet computers are likely by then to become increasingly unsafe for use on the Internet, even though dependence on the Internet will be even greater then. U.S. computer products like microchips incorporating the new bilateral computer architecture would have a clear and sustained competitive market advantage world-wide outside of China.
A Green Technology:
An important additional benefit of new safe Internet computers is that they are naturally clean and green. New system-on-a-chip (SOC) microchip-based personal computers will be naturally far more energy efficient than current many microchip computers. And they will avert an Internet security meltdown, which would otherwise destroy the rapid growth in the Internet virtual world, economic and otherwise, that inherently and increasingly reduces real world fuel consumption and pollution through telecommuting for both work and play.
In conclusion, the new safe Internet bilateral computer architecture can neatly fix the dangerous Internet security situation which we currently face. In contrast, all other known potential computer and network security fixes, even taken together, are far less simple and direct, but also far less comprehensive and far less effective. And far less certain.
The new safe Internet computer architecture is the only solution that solves the basic underlying Internet security problem. All of the alternative solutions are severely limited because they all are built on top of the underlying problem, the obsolete 1945 Von Neumann computer architecture.
SURPRISING ADDITIONAL BENEFITS
SECURE ARCHITECTURE INHERENTLY SUPPORTS PERSONAL POLITICAL FREEDOM:
This leads directly to a surprising and profound political effect of the new security architecture. By developing and manufacturing the single most critical component of a secure and defensible Internet – which will likely be a huge competitive advantage and therefore a mandatory requirement in the competition for success in the future global economy – the U.S. may be creating an inexorable path to freedom and democracy in autocratic countries.
The new bilateral computer architecture is designed to provide Internet security but also provides an unprecedented level of Internet privacy, which is fundamental to individual political and economic freedom.
Although this sounds quite politically naive, it may not be so. The reality may be that any country that opts out of this imminent mandatory technology will suffer the severe economic and military disadvantage of having to rely on a localized Internet that is insecure and indefensible from cyber attack within the borders of that country. A secret backdoor is inherently a potential fatal vulnerability, an access point for hostile intruders, if it becomes known. Therefore any computer security system with a secret backdoor is innately insecure.
This potentially puts a country like China for example in a severe strategic bind. If it builds in secret backdoors in computers and microchips for use by Chinese citizens so that it can monitor and control their political activities, then China may thereby be creating a nation-wide Internet that is made inherently vulnerable and insecure by those secret backdoors.
It may well be the case that to be competitive and safe in an Internet-dominated global economy, all nations will be forced to adopt the new totally secure bilateral computer technology. And that technology allows its citizens the right to extreme privacy and with it a very powerful freedom of private expression in the cyberworld, and thus in effect the real world.
Personal freedom of private expression is perhaps most fundamental of all freedoms, underlying all the other personal freedoms upon which political freedom is based and upon which the individual liberty of each of us depend.
Seen in this light, Apple‘s famous and optimistic Big Brother television advertisement in 1984 may in fact have been prophetic, if just a little premature. Little more than twenty-five years later, and now combined with the Internet, we may have arrived at point where the personal computer connected to the Internet (and its smart cell phone and other descendants) may in only a few years more make tyranny obsolete in the developed and developing world, both economically and militarily.
BUILT-IN PROTECTION FROM THE STAR TREK BORG, THE MATIX AND THE TERMINATOR
Although it might seem very premature now, it may prove later to have been crucial to have made the right basic decisions at this still very early stage in computer and network evolution in order to manage safely the cyberfuture of humans throughout the 21st Century.
Medical device implants into humans have been occurring routinely for many years in the form of heart pacemakers and defibrillators, for example. In the near future, all implanted medical devices will likely be smart devices that incorporate computers with Internet connection. It will be critical for patient safety that the same kind of secure bilateral architecture outlined above is applied also to computers located in the human/machine interface.
Digital implants are now expanding in the direction of direct connection to parts of the human brain. We must therefore adopt now a basic architecture that prevents the potential for human control by machine as seen, for example, in the “resistance is futile” Borg of Star Trek or in theMatrix.
If as some believe the eventual destiny of the human race is to evolve into some merged form of human and computer like a cyborg, we must act now to ensure that we will be free and independent cyborgs, not slaves of the Borg.
In the end, safely protecting the privacy and independence of the human brain from network control is the same as protecting everything that we consider to be ourselves, including that which we call our soul.
We may in fact be rather quickly entering in the next decade or two or more an “Age of Spiritual Machines” as described by Ray Kurzweil where the artificial intelligence of computers surpasses that of humans. If that comes to pass, it may be fundamental to the continued existence of humans that those “spiritual machines” be built on the safe bilateral computer architecture described above.
That essential basic architecture would support the continued human control of computers, however immensely capable they are likely to become. By always providing the human user with preemptive control of an Internet-connected computer, the safe bilateral computer architecture would, for example, provide the capability to prevent the possibility of a Terminator Skynet launching a preemptive war against humans. Clearly, we must not build computer systems that are beyond human control or intervention.
Similarly, robots or replicants or androids with potentially human or superhuman capabilities must be built on the same essential basic Internet-secure binay architecture. In that way we can ensure that they retain their own version of self or soul, independent of control from the Internet; and, in addition, human user preemptive control can be retained.
GNC LICENSING STRATEGY AND BUSINESS PLAN
Since 1996 Global Network Computers has developed an extensive and growing patent portfolio, currently consisting of about ten U.S. patents issued since 2001, with many more applications currently pending. The inventor of the new bilateral computer architecture is Frampton Ellis, a highly successful independent inventor and former member of the Board of Directors of Intellectual Property Owners Association (IPO), as well as runner-up for IPO’s National Inventor of the Year in 1998.
The issued GNC U.S. Patents are as follows:
6,167,428 issued 26 December 2000
6,725,250 issued 20 April 2004
6,732,141 issued 4 May 2004
7,024,449 issued 4 April 2006
7,035,906 issued 25 April 2006
7,047,275 issued 16 May 2006
7,506,020 issued 17 March 2009
7,606,854 issued 30 September 2009
7,634,529 issued 15 December 2009
7,805,756 issued 28 September 2010
7,814,233 issued 12 October 2010
A licensing strategy and business plan is currently under development and not yet completed, but will definitely not include any licensing fees on non-commercial open-source software like Linux, Firefox, and Apache, for example.
Copyright 2010 by Frampton Ellis
